 There have been a number of major security breaches to service in the past few months. It seems like every week we are hearing about a new retailer that has been hacked potentially exposing users financial information. Then there was the iCloud hacks on celebrities and the release of potential DropBox logins through third party applications just the other day. Securing information is becoming a bigger challenge and many companies are starting to implement two factor authentication to accounts. But what exactly is two factor authentication and how does it impact users?
There have been a number of major security breaches to service in the past few months. It seems like every week we are hearing about a new retailer that has been hacked potentially exposing users financial information. Then there was the iCloud hacks on celebrities and the release of potential DropBox logins through third party applications just the other day. Securing information is becoming a bigger challenge and many companies are starting to implement two factor authentication to accounts. But what exactly is two factor authentication and how does it impact users?
More Than Just a Password
The standard security that has been used for online accounts has been the simple password. Most often users will be required to submit a password generally at least six characters long that includes mixed case letters and a number or symbol. The problem is that as computers have gotten faster, the ability to crack even an encoded password is easier. In addition, social engineering by hackers can often allow them to try and circumvent the password and get a new one established so they can get access. With the increasing number of accounts and passwords that people have to use, we tend to use the same login and password information for all their accounts which means that being hacked at one can lead to be hacked at many different services.
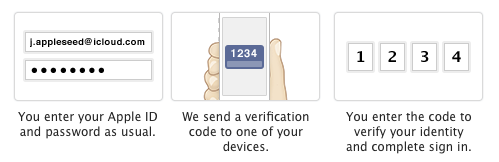
Two factor authentication essentially adds a second level of protection on top of the password. It is also referred to as two-step verification and other names but in essence the idea is the same. When the user establishes the online account and a password, they setup a second level of protection that could be done through several different methods. Often it involves the generation of some form of token or code that is sent to a verified email address, through a text message to a mobile phone or generated through an application such as . The process and method will vary depending upon the services you are using. Failure to provide the code will prevent access to the account or request.
How it Works
Most services require that you setup the two step process when you establish your account but some have implemented it on older accounts or as an option. For instance, when you setup an account, it may prompt you for a cell phone number or email address to send a notification to. In order for the account to be activated, the user must follow a link or enter a code from the generated message. This helps the service provider from being flooded with bogus accounts but also helps protect the users because this same method will be used often whenever a new device (computer, phone, tablet, etc) connects into the service or if the password or account information is changed.
Now this is the most basic of two factor authentication in use. It will certainly help prevent simple attacks on accounts and alert users to problems. For instance, if they get a message that the password is set to be change but they did not request it, someone is accessing their account. This alert and notification can prevent the account from being stolen and also allow the account holder to work with the provider to secure the account. For this method to work properly though, users must make sure that the email address or phone number used for the authentication is always up to date or they may get locked out of their own accounts when they try to do something legitimately but don’t have access to receive the token.
Even More Security
 If you don’t mind the hassle, you can take two step verification either further such that it would be required for every login to a service. This is done by using a token generator for the service in question that is then applied at the time of login. The token would be generated through a hashing system such as the Google Authenticator mentioned above. The token is specific to that login and is only valid for a short while. Failure to supply the proper token through the required application prevents access just as if a password what incorrect.
If you don’t mind the hassle, you can take two step verification either further such that it would be required for every login to a service. This is done by using a token generator for the service in question that is then applied at the time of login. The token would be generated through a hashing system such as the Google Authenticator mentioned above. The token is specific to that login and is only valid for a short while. Failure to supply the proper token through the required application prevents access just as if a password what incorrect.
So why is this more secure? Well, a password is typically static. This means that it can be intercepted or cracked through brute force. The token system is more secure because the information you use to login changes every time. This means that it is much less likely to be hacked. For instance, in the two step verification mentioned in the previous section, if someone gets your password, they still could potentially get access into the service because they have the correct password. In this system, they would not get access unless they had physical access to the token generation plus your other login information.
Why Some People Don’t Like It
Lets face it, the more levels of security that we are required to go through in order to access online accounts, the more inconvenient it is for users. Two factor authentication can be extremely annoying. There are a number of different things that can make it annoying to use. For instance, browser like FireFox and Chrome update frequently. When they do, often you must go through the two step process again as the new browser update is seen as a new device. Token generators can also have issues with fast timeouts such that by the time you get your token and then enter it in, it has already expired requiring you to generate another one.
Regardless of the inconvenience that the two factor system causes, it is going to become a requirement for many system. Any service that has sensitive information such as bank information that carries a high financial liability is going to require it eventually. This it to protect themselves but it is also in the interest of users to also apply it to protect their own assets and information as well.

Pingback: Google Security Key Allows USB Based 2-Step Verfication - Tech for Anyone
Pingback: Just How Effective Is Phishing And How To Avoid It - Tech for Anyone