[Updated to include recent court ruling regarding fingerprint security and police searches.]
The Problem of the Password and Passcodes
There are multiple reasons why both passwords and passcodes are not extremely secure. The two most common issues for password security are length and memorability. Both of these play into how well they can protect against people from accessing your device, accounts or data.
Length is an issue primarily due to how easy it is for an individual or program to break through the security encryption. Lets take a look at passcodes for phones and pins for bank cards. Generally this is just a code of four simple digits. With ten numbers to use in each of the four slots, that provides just 10 to the 4th power or 10,000 possibilities. This makes it possible for a determined human to try all the possible combinations to eventually get through it. A computer could theoretically break that in just seconds. Passwords are a bit more complex as you generally have passwords of around 6 to 12 characters which provides a much larger number of possibilities. Still, the computer power today can brute force these in a relatively short time frame.
Adding extra characters or digits to a passcode or password is an easy way to increase the security. The longer it is, the more possible combinations and the longer it takes for any person or program to break that security. But adding more characters makes memorizing those passwords that much more difficult. Many people use words from the dictionary, names, and slight variations on them in order to make it easy to remember a password especially when it is a long one. This makes it easier for breaking because it reduces the possible combinations if a program or individual uses words from a dictionary rather than random string of characters.
The sheer size and number of passwords we are required to know also causes issues. If someone has trouble remembering them, they tend to write down their passwords. This defeats the purpose of security as there is now a record of them for another individual to find and avoid the whole process of cracking them.
How Biometrics Solves Some of This
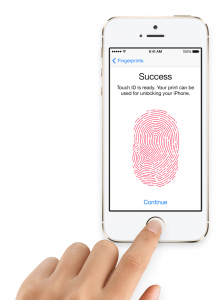
Biometrics is essentially taking the various patterns generated by nature in our own physical bodies to try and avoid using passwords and instead tie security to something like a fingerprint, iris scan or other body dimensions. This is not something that is new as fingerprint scanning has been used for years. The difference is the low cost of producing accurate scanners makes them more viable for inclusion into consumer devices.
The concept here is that by tying access to your device or data to a physically unique item such as a fingerprint means that it is much more difficult to break the security. After all, that biometric signature is unique to a specific individual. Once the device is trained to look for the specific biometric pattern, the user now does not have to remember a password and can instead just swipe their finger instead.
Biometrics Can Still Be Tricked
Security is the prime focus of biometrics. It is much harder for an individual to gain access by trying to replicate a biometric pattern than to try and guess a password. The problem is that it isn’t infallible. Years ago, the Mythbusters aired an episode entitled Crime and Myth-domeanors 2 in which they attempted to trick various fingerprint scanners. Surprisingly, to get access. The process was quite complicated in some instances but still doable.
When Apple released the new TouchID feature, a similar . In a matter of days, a process was verified and tested that could allow an individual to bypass the fingerprint security. Once again, it was a very difficult process but something that is possible.
I’m also reminded of the instances of biometrics previously used by Disney at Walt Disney World for their annual pass holders. When you had an annual pass, you setup a biometric scan of two fingers that would theoretically tie that pass only to that individual. It was setup to try and prevent multiple people sharing a single pass. While it was an interesting idea, the system would often fail and require separate validation by a cast member. That old system has since been replaced by a newer more accurate fingerprint system but it still fails from time to time.
Passwords and Passcodes Live On
Even though the biometrics make access quicker and easier, the passwords are still going to be there. For instance, if a biometric security is setup on a single fingerprint, if the individual injures their hand such that the finger can’t be used, they are unable to access their device or data. This is one of the reasons they suggest having multiple fingers registered from both hands to avoid such a case but even still, there needs to be a way to get access if this doesn’t work. As a result, there is still going to be a backup password or passcode.
In addition to this backup security measure at the device level, the biometric data is generally only stored for a specific point of access such as unlocking your iPhone or logging into a PC. In order for the biometric to be setup with an external service, it is still essentially tied to a login and password for that site similar to what a password manager program would do. Even if the biometric data were to be registered and confirmed via a remote system, that data is still being transmitted and can be compromised through other means similar to how a password would be cracked.
A New Wrinkle
Recently, a Virginia Circuit Court Judge ruled that . This ruling sets a very big precedent regarding law enforcement searches. You see, users were not required to supply a password or passcode to unlock a device on the grounds that it violated the US Fifth Amendment regarding self-incrimination. The Judge essentially stated that this did not apply as a suspect who has had to supply fingerprints to law enforcement and therefore does not gain that protection.
This court case only applies right now to the state of Virginia but it could cause similar issues to come up in other states. It is likely that this or other cases will be appealed to higher courts to challenge the ruling and get biometric information such as fingerprints into the same category as passwords and passcodes.